A simple solution to the private key-loss conundrum
1. Problem
Statistically, over 10% of users forget or lose their passwords or private keys for encrypted data. This is not a big problem if there is a password or private key recovery option, but it becomes a disaster when there is no a way to recover the lost or forgotten password or private key. According to cryptocurrency data firm Chainalysis, over three million bitcoins are considered lost due to forgotten passwords (see [1]). Stefan Thomas, San Francisco-based investor became famous when he revealed that he lost his private key to the hardware based cryptowallet IronKey, which holds 7,002 bitcoins (see [2]). The value of this loss (in dollars) was $479,784,042 on November 5, 2021. The value of losses from lost private keys to encrypted data, files, drives is not possible to estimate accurately.
To avoid such disastrous situations, users may use a simple four step approach to generate easy recoverable private keys, which are based on dynamical passwords.
2. Solution
Dynamical passwords are parametric, dynamic, recoverable, generated on demand, pseudo random passwords, that are not stored in electronic or paper form.
The most important property of dynamical passwords for us is easiness of recovery from some memorable parameters. Most common parameters are: key and date (year, month, day). If, for example, you choose a name and birth date of one of your relatives, friends or some famous persons you will be able to easily recover the password with these parameters.
In this article we learn how to generate recoverable 256-bit private cryptographic keys for bitcoin wallets using public dynamical password generators (DPGs). Our approach consists from the following four steps:
step 1 -define input parameters for the DPG;
step 2 -get dynamical passwords from a public dynamical passwords generator (DPG);
step 3 -select 32 symbols from the dynamical passwords;
step 4 -convert 32 symbols into a 256-bit bitcoin private cryptographic key.
3. Step 1 Define parameters
As a key we use the name of Albert Einstein and as a date his birthday: March 14, 1879.
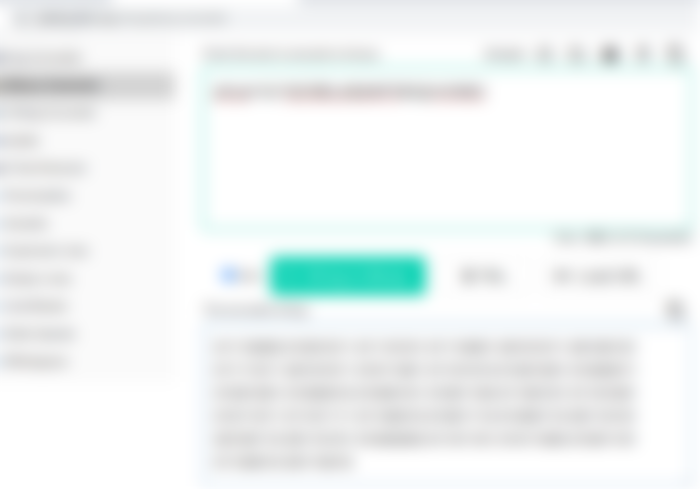
We use a public DPG at URL: https://dynpass.online to generate 20 dynamical passwords as shown on the picture below.

Fig. 1
4. Step 2 -get dynamical passwords from a public dynamical passwords generator
After clicking on the button “Go!”, we get the results shown in the picture below.

Fig. 2
5. Step 3 -select 32 symbols from the dynamical passwords
Now, we combine password No. 9 (20 symbols) with 12 first symbols from the password No. 10. As a result we get the string of 32 symbols.

Fig. 3
6. Step 4 -convert 32 symbols into a 256-bit private cryptographic key
We can use any online string to bits converter, for example such as codebeautify.org/string-binary-converter, to convert the string of 32 symbols into a 256-bit private key, as shown in the picture below.

Fig. 4
For those who would prefer to do this in a linux terminal, the script below will be helpful. You should replace input parameters in the first four rows of the script.
key='test'
day=2
month=2
year=2022
url='https://dynpass.online/dpt/dpt.php'
curl -X POST -F 'key='$key -F 'day='$day -F 'month='$month -F 'year='$year $url >dp.tmp
out=$(awk ‘{if (NR<3) s=s $2;if (NR==3) s=s substr($2,1,2)} END {print s}’ dp.tmp)
echo “Your private key:”
echo $out |perl -lpe '$_=join " ", unpack"(B8)*"
The picture below shows behavior of this script.

Fig. 5
P.S. 1. For 512-bit private keys, 64 characters are required on step 3. For 1024-bit private keys, 128 characters are required on step 3, etc.
2. There are many ways to increase security of this procedure, for example such as:
-select more complex keys;
-use private dynamical password generators;
-use multiple online passwords generators and use output from one as keys for others. There are over 1,000 online passwords generators, over 1 million of pairs, over 1 billion of triplets , over 1 trillion of quartets, etc. Even the most powerful super computer will not be able to test all possibilities in a reasonable amount of time.
In the next post we consider a simple way to defend online accounts against phishing attacks.
7. References
1. Tens of billions worth of Bitcoin have been locked by people who forgot their key.
2. Lost Passwords Lock Millionaires Out of Their Bitcoin Fortunes.
https://www.nytimes.com/2021/01/12/technology/bitcoin-passwords-wallets-fortunes.html