Disclosure: This is a paper I wrote back in 2016. It looks at the Privacy vs. National Security Debate through a Human Geography Lense, hence the Harvard-style References
Introduction
The history of the United States (US) has been traditionally linked to scientific and technological innovation (Nye, 1994). Advancements in the field of cryptology have enabled both the government and privateers to stay ahead of their enemies and competitors. Governments have utilised the encryption software to preserve national security whereas companies have marketed the software to citizens demanding the protection of their privacy, and corporations demanding the safeguarding of their data. The recent debate between Apple Inc. and the Federal Bureau of Investigations (FBI), as well as the public discussion it has stimulated, springs from an amalgamation of perspectives regarding the role of encryption in society. The purpose of this essay is to draw from this debate and comprehend the sociotechnical dynamics of encryption. In doing so, there will be a description of the current debate followed by a brief historical overview of encryption in the US. Thereupon, there will be an analysis of the networks formed within the current case under an Actor-Network Theory (ANT) framework. Thereafter, there will be a co- production analysis divided into three sections: Firstly, the legal environment surrounding encryption will be analysed to facilitate an understanding regarding the atmosphere in which encryption software was developed. Secondly, there will be a section devoted to the use of mobile phones in US society to determine their value and their implication on the routine of US citizens. Thirdly, drawing from the history of technological innovation in the US , this essay will present the sociotechnical imaginaries of encryption technologies, followed by the future implications of this debate.
Description
The Current Debate
The current debate between Apple Inc. and the FBI concerns an iPhone 5c, recovered on December 2015, belonging to Syed Rizwan Farook, one of the terrorists involved in San Bernardino terrorist attack of the same year (Zimmer, 2016). The government was unable to crack the iPhone’s security, and requested that Apple, the phone’s manufacturer, creates a ‘backdoor software’ to provide access to encrypted data in Farook’s iPhone ranging from photos to iMessages – a messaging software shared by all Apple devices that allows for Short Message and Multimedia Message Services (SMS & MMS) over the internet with whoever owns an Apple device (Nakashima, 2016a). In contrast to previous operating systems which required a four-digit numerical password limited to 10,000 possible combinations, the iPhone ran iOS 9, which allowed for an internal six-digit lower-case password consisting of both letters and numbers, a security feature which would require the FBI to spend more than 5 years to crack (Nakashima, 2016a). Additionally, to protect the users’ privacy, iOS 9 has a feature that wipes all data after ten incorrect password entries (ibid). The FBI requested a court order asking for the wiping feature to be removed from the specific iPhone by installing a new operating system on the random access memory of the phone (Blankstein, 2016) under the All Writs Act (Chesney, 2016; Mitchell, 2016; Nakashima, 2016a). The order was granted by Judge Sheri Pym, however it did not account for the viability of such a modification, consequently putting the company in a position where it may face financial penalties regardless of its willingness to cooperate with the aforementioned order (Mitchell, 2016). Apple’s CEO, Tim Cook (2016) issued a statement arguing that Apple is not willing to comply with the FBI’s request for two reasons; firstly, because such a software may hinder the data security of thousands of law abiding customers as the backdoor could be used on multiple phones, and, secondly, because it would establish a legal precedence for all similar cases involving technology companies and encryption software, both locally and globally. Consequently Apple Inc. appealed the court order and built a case arguing that the order violated the company’s first amend rights claiming that code is speech, and in the words of Ted Olson, Apple’s lead attorney, “if we’re saying that there is a serious threat, throw out the constitution in order to prevent that threat, where do we draw the line?” (Segall, et al., 2016). Apple’s position was supported by the ‘Reform Government Surveillance’ movement which consists of leading tech companies such as Microsoft, Google and Facebook (RGS, 2015; 2016). The FBI disputed violation of first amendment rights by asserting that programming code is not a form of speech, to which Apple responded that the government does not understand technology (ibid). At this point a recurring theme arises: Technology changes faster than social norms and conventions, such as laws and constitutions, which leads to a need for increasingly specialized knowledge when addressing how technology advancements affect societal matters and vice versa. Governments and corporations may afford to keep up with these advancements; however common citizens may lag behind, ergo finding themselves vulnerable to an invasion of their privacy. On March 28, the FBI announced that it had managed to access the data on the iPhone, aided by an anonymous third party hackers (Weise, 2016). This development precipitates two even grander debates (Nakashima, 2016b). On the one hand there is the question of the nature of those hackers (ibid). Hackers are traditionally classified into two main groups; ‘white hats’, who uncover the liabilities of software either publicly, or privately to the organisation responsible for its developments, and ‘black hats’, who exploit those vulnerabilities to access networks and purloin personal data (ibid). However, in this case the hackers worked to introduce software vulnerability to a private product, contracted by the government’s needs to gain intelligence, they acted as ‘grey hats’. This is problematic for two reasons. Firstly, there is no clear evidence regarding the hackers’ intention to sell the vulnerability of the software to third parties, endangering the data security of US citizens, due to the reluctance of the FBI to disclose their identity. Secondly, those hackers were paid $1 million of taxpayers’ money, and their work provided little to no value to the investigation, thus raising concerns towards the FBI’s appropriation of funds towards non-traditional projects (Barrett, 2016). On the other hand, the FBI is sceptical regarding whether it should or shouldn’t disclose the flaw with Apple Inc. on the grounds that they may need to prolong this vulnerability so as to exploit it in future terrorist incidents.
It should, at this point be noted that, in April 2015, Michael S. Rogers, the director of the National Security Agency (NSA), suggested that technology companies should be required to “guarantee government access to encrypted data on smartphones and other digital devices” (Nakashima & Gellman, 2015). Edward Snowden (2016) has tweeted that “the FBI is creating a world where citizens rely on Apple to defend their rights, rather than the other way around”. In his book, The Refinement of America: Persons, Houses and Cities, Richard Bushman (1993) illustrates how the US government has promoted individual consumer rights, exemplified by the 2nd amendment right for private ownership of firearms – a right that has more than once backfired against civil security (Greenhouse, 2008). Snowden’s statement on the current debate along with Roger’s statement regarding technology companies are of pivotal importance as they encapsulate, intentionally or not, how the role of the state is shifting from a liberal mind-set of no government intervention to a controlling state that accumulates power and intelligence through technology. As Dolan and Kim (2016) have pointed out this debate is not limited to a specific device in a specific case, but it will potentially establish a precedent in a wider debate of privacy versus national security. John McAfee, the developer of the first commercial antivirus software, has in several instances highlighted the importance of this debate (McAfee, 2016a). Regarding the outcome provided by the third party hackers, he commented that this solution bears no difference to the universal key that Apple refused to provide (Balakrishnan, 2016). Hence, Tim Cook’s dystopian prediction, of a future where consumers’ privacy is threatened, may come to reality, especially when taking into accounts various incidents where US government agencies such as the NSA have been hacked due to backdoors they installed in supposedly secure networks (McAfee, 2016b), exposing the citizens to the number one threat to national security, cyber-attacks (Limitone, 2016).
History of Encryption
Cryptography has been a field of study since 1900BC, as various parties have historically sought to conceal some sort of information (SANS Institute, 2001). Etymologically, encryption derives from the word “κρυφό”, meaning hidden in Greek. In 1929 the American Cryptogram Association was found (Zimmer, 2016). After WW1, William F. Friedman, a renowned US cryptographer was able to break the Japanese ‘Purple’ cipher (Kahn, 1996). However, the field sustained an exponential change during WW2, when the allied forces sought to decrypt the German Enigma Cipher, primarily through the work of Marian Rajewski and Alan Turing, who built one of the first analogue decryption computers (SANS Institute, 2001). Post WW2, encryption and cryptography were clearly rooted in US governance policies. An extremely influential figure in science and technology studies was Vannevar Bush, an MIT educated engineer that became a policy advisor to the US government, and made several recommendations to President Franklin D. Roosevelt regarding the importance of scientific research for the advancement of the American Society (Zachary, 1997). Consequently, encryption played a crucial role during the Cold War as it effectuated the NSA’s formation in 1952 under President Truman, an agency that came into being with the objective to monitor surveillance and global communications to avert a crisis such as the Pearl Harbor incident (Johnson, 2008). In the report, several intelligence agency rivalries are present especially between CIA and the NSA regarding the nature of surveillance and the manner in which the data collected will be used (ibid). David Kahn (1996) devotes an entire chapter of his book on the history of cryptography to depict how the NSA was developing surveillance technologies observing individuals and government/corporate bodies both within and outside the US. It should at this point be noted that when googling a summary of this book, the first result was a review posted by the CIA library written by Roger Pineau (1996), who expresses scepticism towards the majority of Khan’s sources. Within the book, and the review itself, it is stated that British intelligence dissuaded Khan from revealing all the evidence he had gathered on British cryptology, and it is logical to assume that the US intelligence agencies might have also tampered with the content of the book, especially since the first edition was published in 1967, an era when the internet was not widely used (ibid). Similarly, many segments of Johnson’s report are redacted, leading to the conclusion that government sources on the history of encryption in the US do not provide the entire story.
Actor-Network Theory
Throughout the history of science and technology studies, two main understandings have been clashing; social determinism, the view that society shapes technology, and technological determinism, the view that technology shapes society (Tatnall & Gilding, 1999). However, ANT, developed by Michael Callon, Bruno Latour and John Law provides us with an analytical framework in which neither view is privileged, offering an imaginary wherein society, denoted as human actors, and technology, denoted as non-human actors, are entangled in a network of correlations that determines those actors’ identities (Tatnall & Gilding, 1999; Cressman, 2009). ANT is built on the axiom of ‘generalised symmetry’, a conception that cognizes the heterogeneity of human and non-human actors, whilst acknowledging gravity of both actors in the formation of social dynamics (Callon, 1986).

Figure 1 depicts some of the actors in the Apple vs. FBI debate described previously, and the network(s) they form. When software engineers coded the encryption software, as well as the feature that wipes the iPhone to protect data security, their identity was not limited to the advancement of technology. They were simultaneously ‘sociologist engineers’ that engaged in the process of ‘heterogeneous engineering’ as they affected the sociotechnical reality by concurrently producing new software, thus designing novel technology, and by designing a social world wherein personal data could be safeguarded (Callon, 1987; Law, 1987). The property of ‘secret keeping’ that would otherwise be attributed to a friend or family member, a human actor, is ‘translated’ into the iPhone, a fusion of software and hardware that constitutes a non-human actor, which has become the ‘delegate’ of this property (Latour, 1992). ANT is often concerned with natural sciences research and laboratories (Latour & Woolgar, 1979). It describes laboratory equipment as ‘inscription devices’ that transform matter into text (ibid). The value of those devices is that they partake in a process of classifying and translating natural findings into numbers and graphs that may be understood by a plethora of human actors. On a similar note, the order of Judge Sheri Pym may be interpreted as an inscription device that instructs different human and non-human actors on how they should behave. Another noteworthy observation of ANT is the value of ‘network effects’ (Bosco, 2006). The behaviour of actors within networks determines the nature of those networks, hence Judge Pym’s order, requiring Apple to alter the behaviour of their employees to assist the FBI investigation, would not solely affect the actors themselves, or the network within the company, but also the an external network of human and non-human actors that interact with Apple, as well as all future cases that may involve a similar piece of technology. Moreover, the process of ‘punctualisation’ proposes that actor-networks may be ‘black-boxed’, decomposed as technological artefacts and analysed as nods in grander networks (Cressman, 2009). The figure above only illustrates a network within the case study at hand. It is therefore significant to appreciate how any development within the specific network might affect other aspects of the sociotechnical sphere.
Co-Production
Legal Environment
Vannevar Bush was a key player in reshaping American science policy both during the war, but especially in the post-war era (Dennis, 2004). In 1945, he delivered to President Franklin D. Roosevelt “Science, The Endless Frontier” a report where he “conceptualized science as part of a larger problem: the nature of postwar American state” (Dennis, 2004, p. 228). Many argue that this altered the US’s perception of science in society as he underlined “the interconnectedness [...] of politics, science and social order” (ibid). The beginning of WW2 found America to be importing scientific and technological knowledge from Western Europe, however the war prevented the production of knowledge in those geographies, hence a need to fund research in American universities emerged (Dennis, 2004). The Manhattan project elucidated the perils of direct armed conflict, hence the Coordinating Committee for Multilateral Export Controls (COCOM) was founded so as to protect the secrecy of technologies associated with both munitions and commercial uses (Yashura, 1991). The beginning of the Cold War found encryption to be demanded primarily by the military, thus the export of encryption ‘know-how’ was regulated through COCOM, however the rise of finance in the 1970s generated a need for encryption software in the private sector which was answered by the establishment of the Data Encryption Standard contracted to IBM (Tuchman, 1997). Importantly, it was President Clinton’s order 13026 that shifted commercial encryption software from military to commercial control (Clinton, 1996). Since the mid-1990s the legal landscape around cryptography has been constantly changing with an array of legislations, bills and through various cases (Koops, 2013). The legal environment revolves around import and export controls, patents, as well as issues regarding the conditions under which private citizens or other entities should allow for, or facilitate the decryption of data (ibid). Specifically, the Digital Millennium Copyright Act, of 1998, “creates penalties for circumventing copyright-protection systems” (ibid). Regarding imports of encryption software there is no regulation in the US, however the export of encryption software is divided into two categories; national security and commercial cases (ibid). Export regulations have been loosening since 1996, as the National Research Council published a study promoting the commercial use of encryption, arguing for reduced state intervention on cryptography in the private sector (ibid). A case that altered US export restrictions on cryptography was Bernstein v. Department of Justice (Dame-Boyle, 2015). In short, the court ruled that the administration’s export regulations that prevented Daniel Bernstein from publishing an encryption algorithm online, violated his 1st Amendment rights as they deprived him of free speech (ibid). This ruling is of particular importance to the Apple v. FBI case as it provided a legal precedent on which Apple based its motion to vacate Judge Pym’s order, arguing that it “amounts to compelled speech and viewpoint discrimination in violation of the First Amendment” (Solomon, 2016).

Use of Smartphones in Society

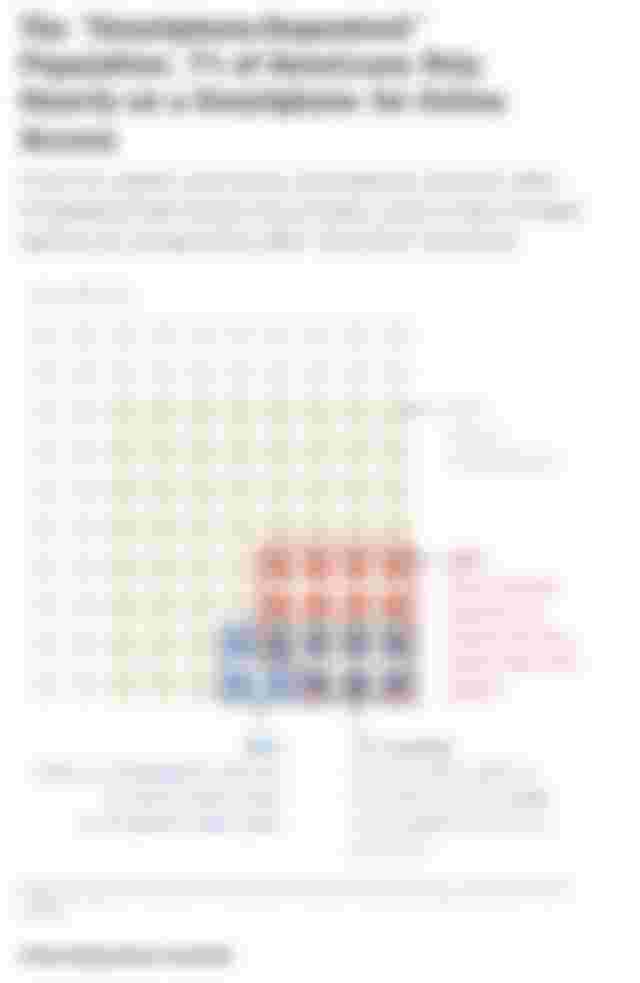
As illustrated in Figure 2, mobile phones are intertwined with the fundamental aspects of US citizenship (Smith, 2015). We should clarify that the smartphones are much more advanced than traditional mobile phones, as they are similar to laptops or desktop computers in that they allow the user to access the internet and perform various tasks. There are apps created by the company that markets the smartphone, however leading companies, such as Apple, tend to encourage third parties to design applications for their products and market them through e-shops (Jobs, 2007). Technological and social orders are being produced together (Jasanoff, 2004a).The idiom of co-production describes a process wherein scientific knowledge is produced within a societal network of norms, conventions, rules and laws (ibid). This network is, in turn, altered by advancements in the scientific fields (ibid). However, co-productive accounts are traditionally concerned with natural sciences, their impact on society and vice versa (Jasanoff, 1996; Jasanoff, 2004a; Jasanoff, 2004b). Although computer science is not a natural science per ce, we could utilise a co-productive approach to the subject given the rapid advancements on the field and theorisations regarding the ‘Technological Singularity’ – a time in which artificial intelligence will enable the future of man and computer to merge (Vinge, 1993). Although, such theorisations have been a field of dispute, we should only take into account that they stem from an undeniable realisation: computer science is a field advancing exponentially, and it is ineludibly revamping the landscape of social reality. Encryption software was created due to social needs of privacy and confidentiality. The ‘sociologist engineers’ that programmed the iPhone’s security features were driven by a social demand for increased data security. Although the privacy of US citizens was fortified, the malicious use of this technology by criminal groups such as terrorists, concealing their communications, often renders society unable to defend itself against threats, steering our analysis to the understanding that technology impacts society, in that it may hinder the state’s capacity to preserve national security. Consequently, the implementation of the ‘grey hats’ solution may be interpreted as an incident in which society once again alters technology. In general, we may deduce that society and technology co-produce aspects of our sociotechnical reality and that cases such as the one discussed in this essay extend to broader, often conflicting issues, such as the preservation of privacy and national security. President Barack Obama addressed these issues, suggesting that both parties, the Government and Apple Inc., should ‘co- produce’ a solution in which strong encryption does not undermine national security commenting that he is “way on civil liberties side of this thing” (Obama, 2016). In contrast, Donald Trump, the republicans’ leading candidate, has taken a much more absolute stance in the matter, asking consumers to boycott Apple until it cooperates with the FBI (CNN, 2016).
Sociotechnical Imaginaries of Encryption Technology
David E. Nye (1990; 1994) has argued that Americans draw their identities from the nation’s technological achievements over time highlighting the social, political, cultural and economic embeddedness of technological innovation. He describes how the ‘technological sublime’ – a term describing the “sense of awe and disorientation that we experience in the presence of some gigantic structure or immensely powerful machine” (Jeffrey, 1995, p. 85) – was transformed from an artistic representation of technological innovation to an articulation of the American consciousness of exceptionalness (Nye, 1994). New technologies have, essentially, been sources and emblems of national pride, “fundamental to building the state, both as literal articulations of power and as legitimizing structures” (Nye, 2006, p. 162). It is important to understand that while humanity has been involved in technological innovations to increase either safety or efficiency, those innovations often result to unpredicted accidents or disasters (Nye, 2006). Furthermore, Nye underlines that “technology is man’s reaction upon nature or circumstance and that it leads to the construction a new nature, a supernature imposed between man and original nature” (2006, p. 190). This ‘supernature’ is apparent in our current debate, we can thus construct a ‘sociotechnical imaginary’ of encryption technology, “descriptive of attainable futures and prescriptive of the kinds of futures that ought to be attained” (Jasanoff, et al., 2007, p. 1). Technological innovation has allowed for the formulation of a new reality, a new geography in some cases, wherein values such as data security may be preserved and safeguarded in an imaginary ‘cyber-vault’. This overdependence often facilitates the immersion in a supernatural reality in which individuals neglect the existence of the ‘original nature’ and the social dynamics external to this supernature. On a larger scale, this might lead us to two equally dystopic scenarios. On the one hand, it might lead to an Orwellian future in which the state or government enforces draconian measures, sacrificing values such as privacy and diversity on the altar of natural security, implementing policies of extreme and total surveillance, propaganda and so on. One can at this point appreciate the tragic irony of Apple’s 1984 advertisement in which the company promises a future that will bear no similarity to George Orwell’s 1984 (Cole, 2010). On the other hand, it might lead to an actuality of pure anarchy, where the state has succumb to cyber-attacks or terrorist incidents, leading to the eradication of any effective form of governance and the technological return to the ‘dark ages’. Although both scenarios might have crossed the realm of science fiction, the inevitability of some of their aspects cannot be underemphasized. We are therefore in a dire need for the cooperation of the social sphere, including government agencies, judiciary systems and policymakers, and the technological sphere, including technology companies, software and hardware engineers. The inadequacy of the current legal system is apparent as both its rules and its employees seem to be lagging behind advancements in technology, hence the aid of the tech community is required for the establishment of new frameworks under which both privacy and security may be preserved simultaneously to avoid the perils of any dystopian future.
Conclusion
Concluding, encryption has been a matter of diachronic significance to the history of the US. A revision of the debate between Apple Inc. and the FBI encapsulates the multifarious technological and social dimensions of this technology, especially regarding its implications for civil liberties and matters of the state. ANT has been essential in deconstructing the processes and interactions that formulate between various actors within the current debate, thus providing a clear representation of the réseau of sociotechnical dynamics. The legal environment vis-à-vis encryption software as well as the co-production of smartphones in society speak of those technologies’ significance. All things considered, the manner in which this dispute will be resolved will provide a precedent for similar cases, establishing the modus operandi for the co-production of encryption technologies and society. The purpose of this essay was not to vilify or sanctify either party, but to highlight the gravity of fortifying citizens’ privacy while preventing the co- production of terrorist, or other criminal cultures, globally. However, “power tends to corrupt, and absolute power corrupts absolutely” (Dalberg-Acton, 1887), an independent authority should thence ensure that neither a government nor a corporation abuses this power. Given the novelty of this debate, there is not sufficient research on the subject, especially from a STS perspective. Academics, along with trained professionals and experts should provide an interdisciplinary, integrated solution to this disharmony so as to prevent it from hindering either privacy or national security.
A big thank you to my sponsors:
Bibliography
Balakrishnan, A., 2016. McAfee: I know who's helping the FBI hack Apple. [Online] Available at: http://www.cnbc.com/2016/03/22/john-mcafee-speaks-out-on-fbi-apple-hacks-third- party.html
[Accessed 20 April 2016].
Barrett, D., 2016. FBI Paid More Than $1 Million to Hack San Bernardino iPhone. [Online] Available at: http://www.wsj.com/articles/comey-fbi-paid-more-than-1-million-to-hack-san-bernardino- iphone-1461266641
[Accessed 21 April 2016].
Blankstein, A., 2016. Judge Forces Apple to Help Unlock San Bernardino Shooter iPhone. [Online] Available at: http://www.nbcnews.com/storyline/san-bernardino-shooting/judge-forces-apple-help- unlock-san-bernardino-shooter-iphone-n519701
[Accessed 2 April 2016].
Bosco, F. J., 2006. Actor network theory, networks and relational approaches in human geography. In: S. Aitken & G. Valentine, eds. Approaches to Human Geography. London: Sage Publications, pp. 136-146.
Bushman, R., 1993. The Refinement of America: Persons, Houses and CIties. New York: Random House.
Callon, M., 1986. The Sociology of an Actor-Network: The case of the Electric Vehicle. In: M. Callon, J. Law & A. Rip, eds. Mapping the Dynamics of Science and Technology: Sociology of Science in the real World. London: MacMillan Press, pp. 19-34.
Callon, M., 1987. Society in the Making: The Study of Technology as a Tool For Sociological Analysis. In: W. E. Bijker, T. P. Hughes & T. F. Pinch, eds. The Social Construction of Technological Systems. Cambridge, MA: MIT Press, pp. 83-106.
Chesney, R., 2016. Apple vs FBI: The Going Dark Dispute Moves from Congress to the Courtroom. [Online] Available at: https://lawfareblog.com/apple-vs-fbi-going-dark-dispute-moves-congress-courtroom [Accessed 26 March 2016].
Clinton, B., 1996. Executive Order 13026 of November 15, 1996: Administration of Export Controls of Encryption Products. Federal Register: Presidential Documents, 61(224), pp. 58767-58768.
CNN, 2016. Donald Trump: Boycott Apple if they don't help FBI. [Online] Available at: https://www.youtube.com/watch?v=uJmUlh5beLc [Accessed 20 April 2016].
Cole, R., 2010. Apple 1984 Super Bowl Commercial Introducing Macintosh Computer. [Online] Available at: https://www.youtube.com/watch?v=2zfqw8nhUwA [Accessed 20 April 2016].
Cook, T., 2016. A Message to Our Customers. [Online] Available at: http://www.apple.com/customer-letter/
[Accessed 17 February 2016].
Cressman, D., 2009. A Brief Overview of Actor-Network Theory: Punctualization, Heterogenous Engineering & Translation [Online] Available at: http://summit.sfu.ca/item/13593 [Accessed 28 February 2016].
Dalberg-Acton, J., 1887. Letter to Archbishop Mandel Creighton. [Online] Available at: http://history.hanover.edu/courses/excerpts/165acton.html
[Accessed 20 April 2016].
Dame-Boyle, A., 2015. EFF at 25: Remembering the Case that Established Code as Speech. [Online] Available at: https://www.eff.org/deeplinks/2015/04/remembering-case-established-code-speech [Accessed 20 April 2016].
Dennis, M. A., 2004. Reconstructing sociotechnical order: Vannevar Bush and US science policy. In: S. Jasanoff, ed. States of Knowledge: The Co-Production of Science and Social Order. London: Routledge, pp. 225-253.
Dolan, M. & Kim, V., 2016. Apple-FBI fight over iPhone encryption pits privacy against national security. [Online]
Available at: http://www.latimes.com/business/la-me-fbi-apple-legal-20160219-story.html [Accessed 2 April 2016].
Elite NWO Agenda, 2015. IPHONE ENCRYPTION BATTLE - Iphone Encryption Is So Good, COps Cant Get Past It. [Online] Available at: https://www.youtube.com/watch?v=67oans5gsjk [Accessed 10 April 2016].
Greenhouse, L., 2008. Justices Rule for Individual Gun Rights. [Online] Available at:
http://www.nytimes.com/2008/06/27/washington/27scotuscnd.html?_r=1&pagewanted=all [Accessed 20 April 2016].
Jasanoff, S., 1996. Beyond epistemology: relativism and engagement in the politics of science. Social Studies of Science, 26(2), pp. 393-418.
Jasanoff, S., 2004a. The idiom of co-production. In: S. Jasanoff, ed. States of Knowledge: The Co- Production of Science and the Social Order. London: Routledge, pp. 1-12.
Jasanoff, S., 2004b. Ordering knowldege, ordering society. In: States of Knowledge: The Co-Production of Science and Social Order. London: Routledge, pp. 13-45.
Jasanoff, S., Kim, S.-H. & Sperling, S., 2007. Sociotechnical Imaginaries and Science and Technology Policy: A Cross-National Comparison. Cambridge, MA: NSF Research Project, Harvard University.
Jeffrey, K., 1995. [Review of American Technological Sublime]. Environmental History review, 19(2), pp. 85-87.
Jobs, S., 2007. Third Pary
Available http://web.archive.org/web/20080218214950/http://developer.apple.com/iphone/devcenter/third_party_apps.php
[Accessed 20 April 2016].
Johnson, T. R., 2008. American Cryptology during the Cold War, 1945-1989, Washington: National Security Agency.
Kahn, D., 1996. The Codebreakers: The Story of Secret Writtig. 2nd ed. New York: Scribner.
Koops, B.-J., 2013. Cryptography Law: Overview per country. [Online] Available at: http://www.cryptolaw.org/cls2.htm#us [Accessed 20 April 2016].
Latour, B., 1992. What Are the Missing Masses? The Sociology of a Few Mundane Artifacts. In: W. E. Bijker & J. Law, eds. Shaping Technology/Building Society: Studies in Sociotechnical Change. Cambridge, MA: MIT Press, pp. 225-258.
Latour, B. & Woolgar, S., 1979. Laboratory Life: The Construction of Scientific Facts. Beverly Hills: Sage.
Law, J., 1987. Technology and Heterogeneous Engineering: The Case of Portuguese Expansion. In: W. E. Bijker, T. P. Hughes & T. F. Pinch, eds. The Social Construction of Technological Systems: New Directions in the Sociology and History of Technology. Cambridge, MA: MIT Press, pp. 111-134.
Limitone, J., 2016. Fmr. NSA, CIA Chief Hayden Sides with Apple Over Feds. [Online] Available at: http://www.foxbusiness.com/features/2016/03/07/fmr-nsa-cia-chief-hayden-sides-with- apple-over-feds.html
[Accessed 20 April 2016].
McAfee, J., 2016a. Why Apple vs. The FBI Matters To Everyone (CNBC Interview). [Online] Available at: https://www.youtube.com/watch?v=32c-JBVgZPw [Accessed 20 April 2016].
McAfee, J., 2016b. JOHN MCAFEE: The NSA's back door has given every US secret to our enemies. [Online]
Available at: http://www.businessinsider.com/john-mcafee-nsa-back-door-gives-every-us-secret-to- enemies-2016-2?IR=T
[Accessed 20 April 2016].
Mitchell, A. P., 2016. Full Explanation of Court Order to Apple to Unlock San Bernardino Shooters’ iPhone and Apple Refusal (Full text of court order and Tim Cook’s letter included). [Online] Available at: https://www.theinternetpatrol.com/full-explanation-of-court-order-to-apple-to-unlock-san- bernardino-shooters-iphone-and-apple-refusal-full-text-of-court-order-and-tim-cooks-letter-included/ [Accessed 25 March 2016].
Nakashima, E., 2016a. Apple vows to resist FBI demand to crack iPhone linked to San Bernardino attacks. [Online]
Available at: https://www.washingtonpost.com/world/national-security/us-wants-apple-to-help-unlock- iphone-used-by-san-bernardino-shooter/2016/02/16/69b903ee-d4d9-11e5-9823- 02b905009f99_story.html
[Accessed 10 April 2016].
Nakashima, E., 2016b. FBI paid professional hackers one-time fee to crack San Bernardino iPhone. [Online]
Available at: https://www.washingtonpost.com/world/national-security/fbi-paid-professional-hackers- one-time-fee-to-crack-san-bernardino-iphone/2016/04/12/5397814a-00de-11e6-9d36-33d198ea26c5_story.html
[Accessed 20 April 2016].
Nakashima, E. & Gellman, B., 2015. As Encryption spreads, U.S. grapples with clash between pricavy, security. [Online] Available at: https://www.washingtonpost.com/world/national-security/as-encryption-spreads-us- worries-about-access-to-data-for-investigations/2015/04/10/7c1c7518-d401-11e4-a62f- ee745911a4ff_story.html?tid=a_inl
[Accessed 10 April 2016].
Nye, D. E., 1990. Electrifying America: Social Meanings of a New Technology, 1880-1940. Cambridge, MA: MIT Press.
Nye, D. E., 1994. American Technological Sublime. Cambridge, MA: MIT Press.
Nye, D. E., 2006. Technology Matters: Questions to Live With. Cambridge, MA: MIT Press. Obama, B., 2016. Obama Explains The Apple/FBI iPhone Battle [Interview] (11 March 2016).
Pineau, R., 1996. The Codebreakers: The Story of Secret Writing by David Kahn. Book review by Roger Pineau. [Online] Available at: https://www.cia.gov/library/center-for-the-study-of-intelligence/kent- csi/vol12i3/html/v12i3a09p_0001.htm
[Accessed 20 April 2016].
RGS, 2015. Reform Government Surveilance: Global Government Surveillance Reform. [Online] Available at: https://www.reformgovernmentsurveillance.com/ [Accessed 20 April 2016].
RGS, 2016. Reform Government Surveillance statement on the filing of amicus briefs in support of Apple. [Online]
Available at: http://reformgs.tumblr.com/post/140411522597/reform-government-surveillance- statement-on?is_related_post=1
[Accessed 20 April 2016].
SANS Institute, 2001. History of Encryption. [Online] Available at: https://www.sans.org/reading-room/whitepapers/vpns/history-encryption-730 [Accessed 20 April 2016].
Segall, L., Pagliery, J. & Wattles, J., 2016. FBI says it has cracked terrorist's iPhone without Apple's help. [Online]
Available at: http://money.cnn.com/2016/03/28/news/companies/fbi-apple-iphone-case- cracked/index.html
[Accessed 20 April 2016].
Smith, A., 2015. U.S. Smartphone Use in 2015. [Online] Available at: http://www.pewinternet.org/2015/04/01/us-smartphone-use-in-2015/ [Accessed 20 April 2016].
Snowden, E., 2016. The @FBI is creating a world where citizens rely on #Apple to defend their rights, rather than the other way around. [Online] Available at: https://twitter.com/Snowden/status/699984388067557376
[Accessed 20 April 2016].
Solomon, B., 2016. Apple To FBI: Forcing Us To Unlock iPhone Violates Free Speech. [Online] Available at: http://www.forbes.com/sites/briansolomon/2016/02/25/apple-to-fbi-forcing-us-to-unlock- iphone-violates-free-speech/#13398e9548a1
[Accessed 20 April 2016].
Tatnall, A. & Gilding, A., 1999. Actor Network Theory and Information Systems Research. [Online] Available at: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.10.1265&rep=rep1&type=pdf [Accessed 28 February 2016].
Tuchman, W., 1997. A brief history of the data encryption standard. In: D. E. Denning & P. J. Denning, eds. Internet Besieged: Countering Cyberspace Scofflaws. New York: ACM Press, pp. 275-280.
Vinge, V., 1993. Vision-21: Interdisciplinary Science and Engineering in the Era of Cyberspace. [Online] Available at: https://docs.google.com/file/d/0B-5-JeCa2Z7hN1RfRDlqcXpVYzA/edit [Accessed 20 April 2016].
Weise, E., 2016. Apple v FBI timeline: 43 days that rocked tech. [Online] Available at: http://www.usatoday.com/story/tech/news/2016/03/15/apple-v-fbi-timeline/81827400/ [Accessed 20 April 2016].
Yashura, Y., 1991. The Myth of Free Trade: The Origins of COCOM. The Japanese Journal of American Studies, 4(1), pp. 127-148.
Zachary, G. P., 1997. Endless Frontier: Vannevar Bush, Engineer of the American Century. New York: The Free Press.
Zimmer, B., 2016. Encryption, From Nazis to iPhones. [Online] Available at: http://www.wsj.com/articles/encryption-from-nazis-to-iphones-1458312000 [Accessed 12 April 2016].