Note
This is the tenth assignment from my Masters Advanced Network Security Course which has never been published anywhere and I, as the author and copyright holder, license this assignment customized CC-BY-SA where anyone can share, copy, republish, and sell on condition to state my name as the author and notify that the original and open version available here.
1. Introduction
Reverse Engineering is the process of disassembling and examination to study the parts of (something) to see how it was made and how it works so that you can make something that is like it [1]. As I read in [2] in came back to me that I've actually done a lot of half reverse engineering, where I disassembled camera's, laptops, PCs, hard drives, mouse, and monitors, that would be a full reverse engineering if I thoroughly study them and remade them. There are items that I successfully reversed engineering which are adapters and Cisco router's console cable. For the adapter I just need to buy the parts on electronic shops and assemble. The Cisco router's console cable was almost the same where I disassemble the cable and see how the order of each cables are connected. Then I proceed to a shop and bought 2 DB9 male and female pins, a few cables, and cover, with later I proceed in soldering the cables and made my own console cable as on Figure 1.

Figure 1. My example of Cisco's Router Console Cable Reversed Engineered
A process that was originally applied only to hardware, reverse-engineering is now applied to software, databases and even human DNA. Reverse-engineering is especially important with computer hardware and software. Around 1980s San Jose-based Phoenix Technologies Ltd reversed engineered an IBM's bios in order to make their own original compatible PC to IBM. Cyrix Corp and Advanced Micro Devices Inc reversed engineered Intel Corp microprocessors to make their own cheaper microprocessors [2].
2. Reverse Engineering In Computers
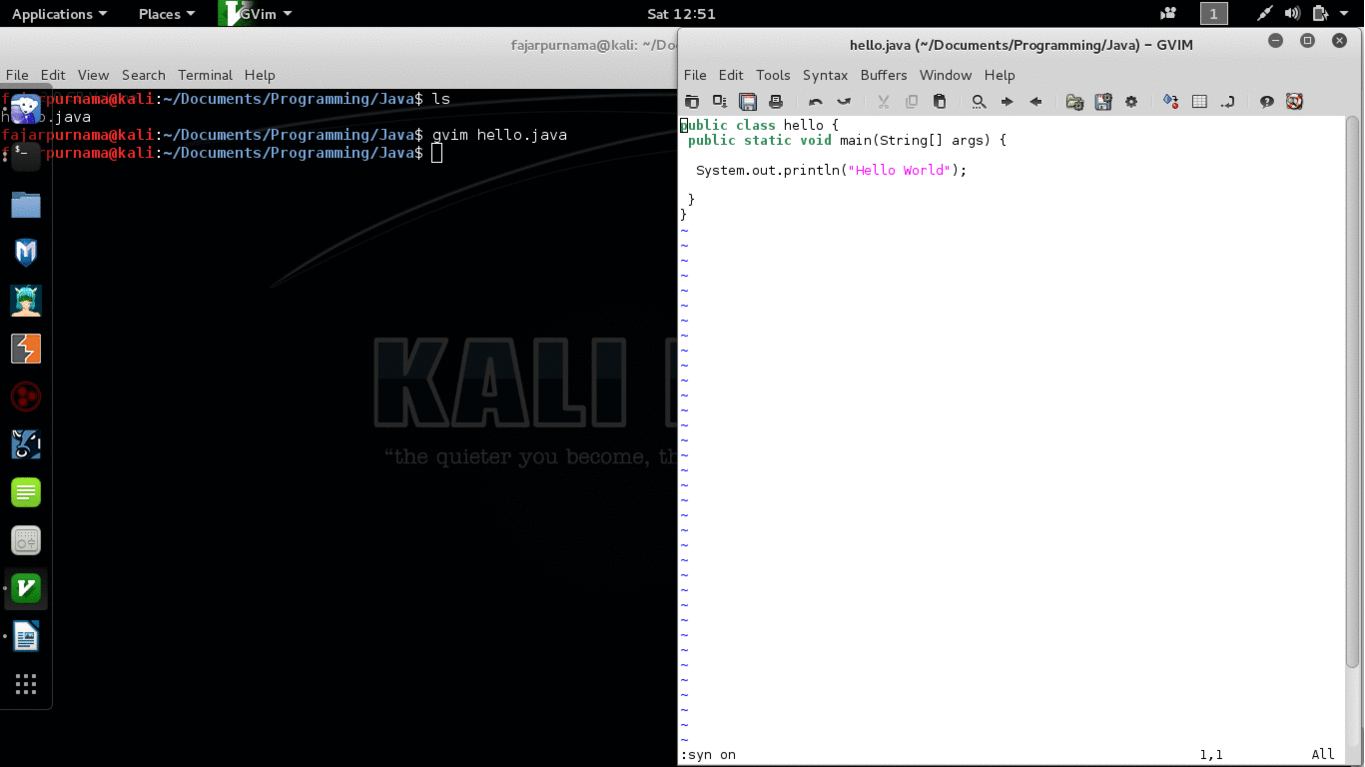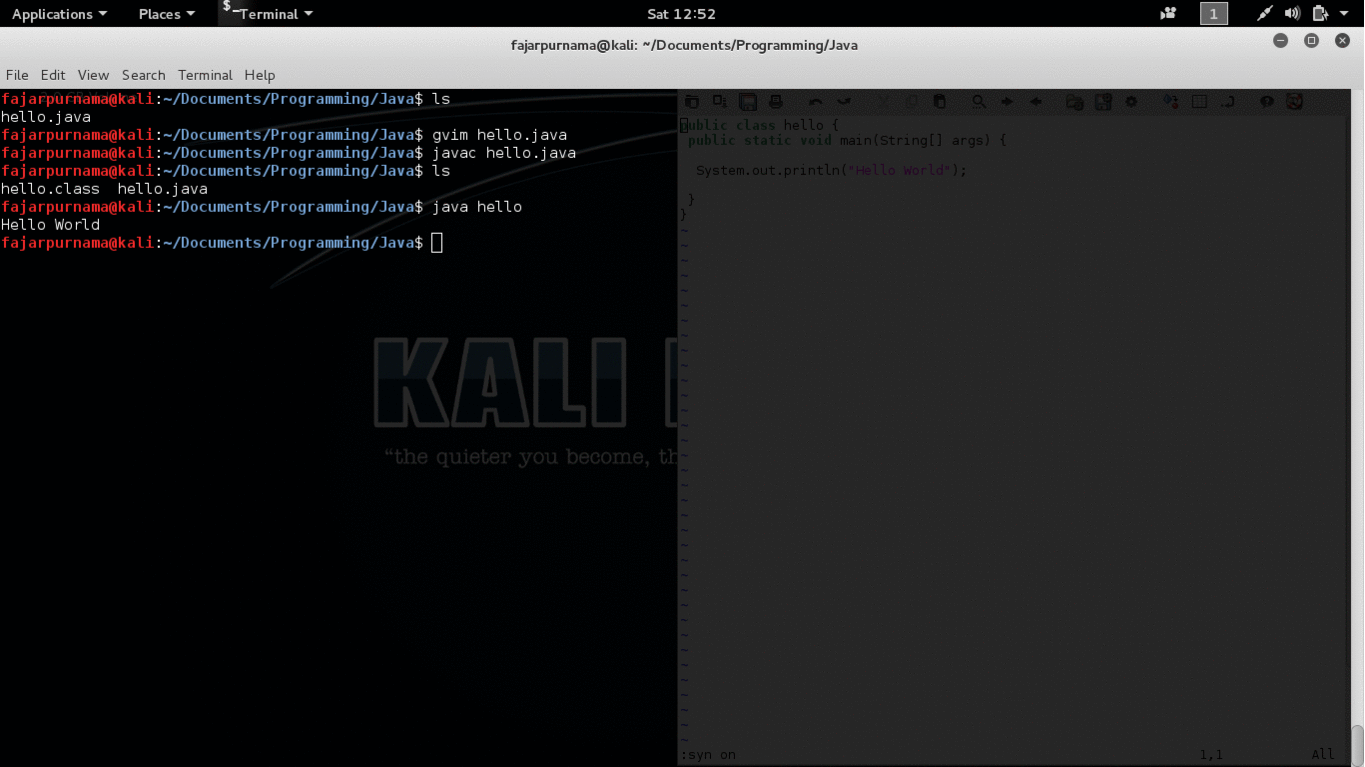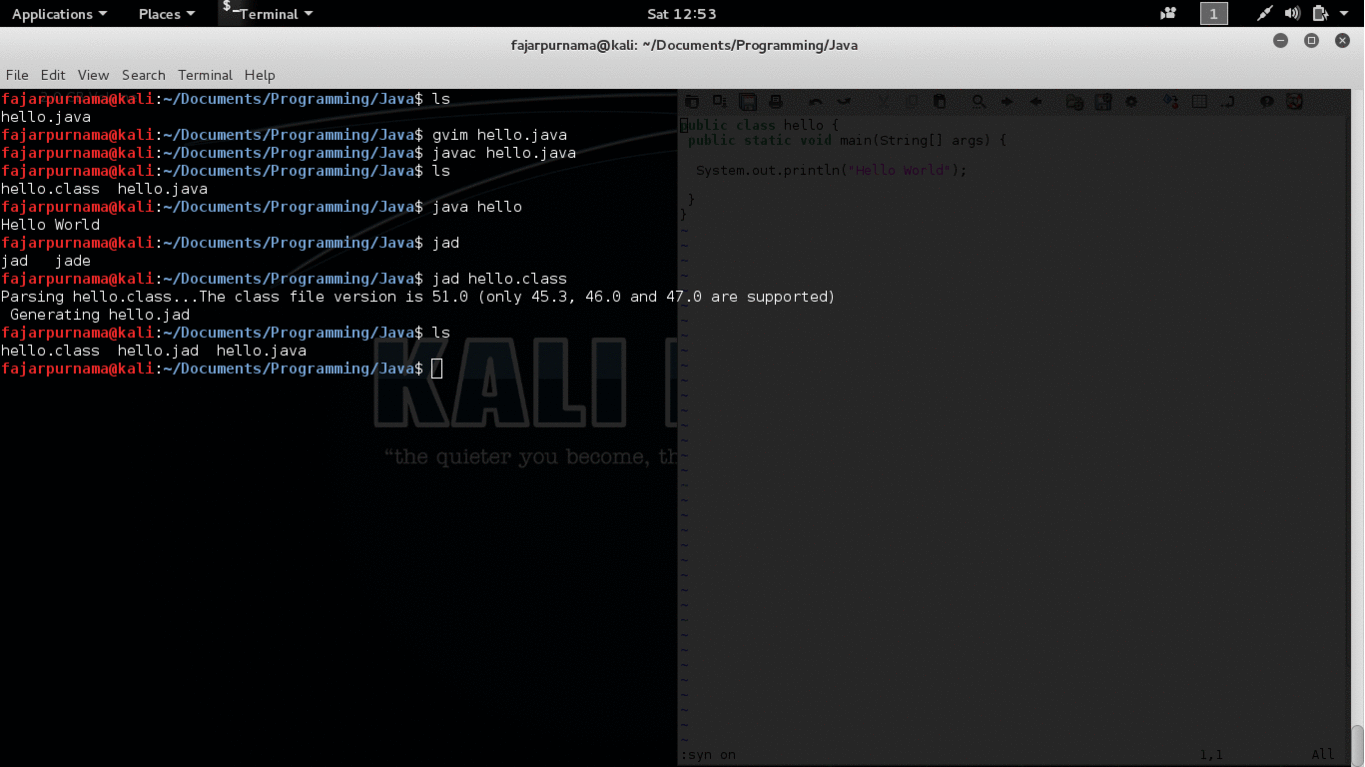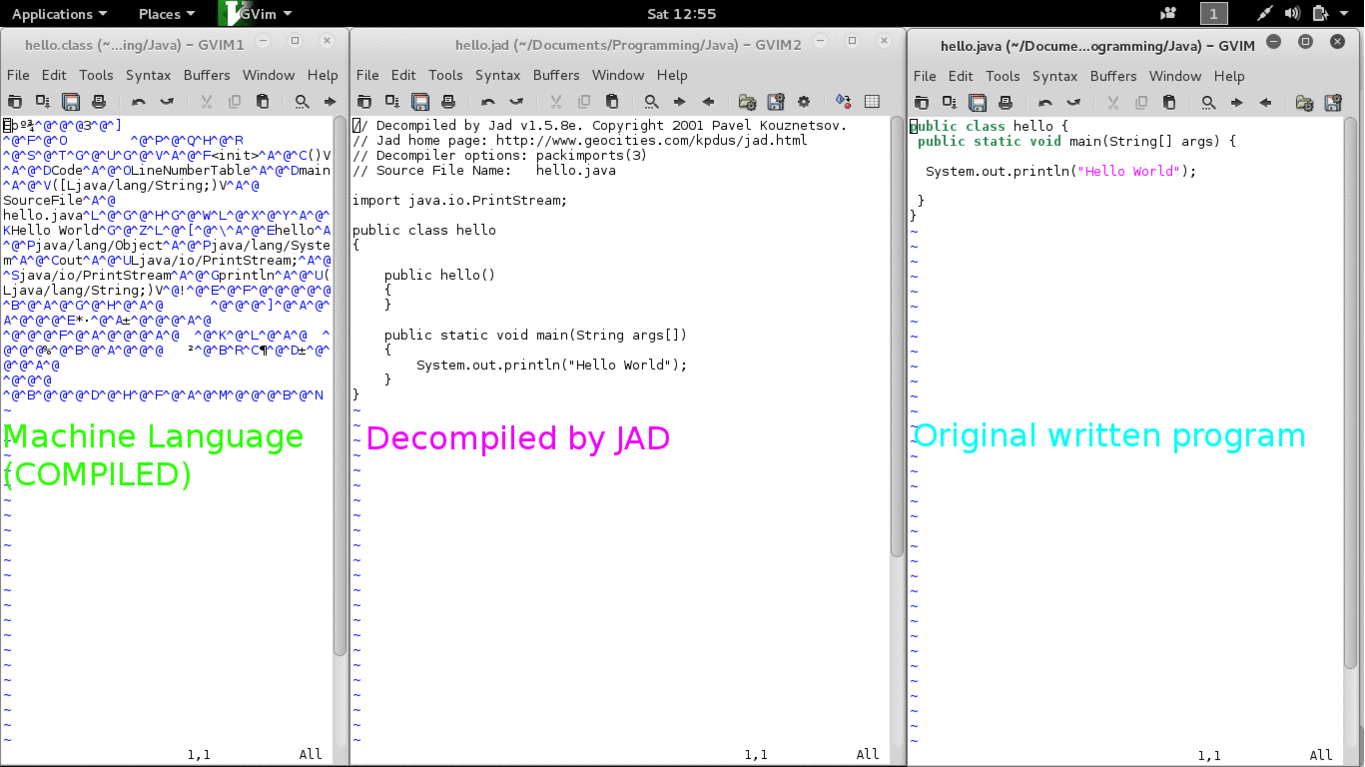
Most programs are written in high level programming language such as C and Java. The written program is then compiled using a compiler into machine language mainly consist of 0s and 1s which then can be executed. This machine language is very difficult for us to understand, but still there are ways to decompile them into high programming language using a decompiler. For example on the GIF picture on Figure 2 I wrote a “hello world” program in java and compiled into “hello.class”. Using an application called “jad” I can decompile the executable file back into the java language.
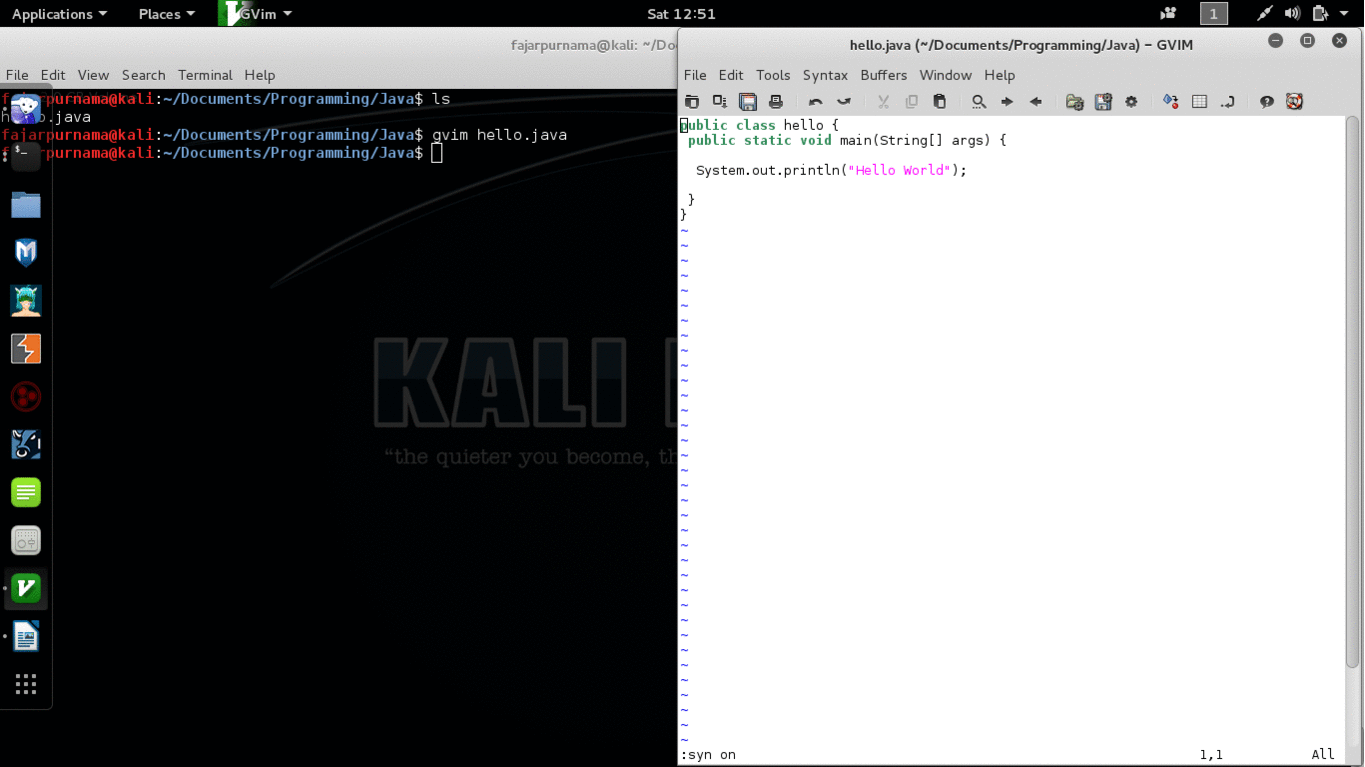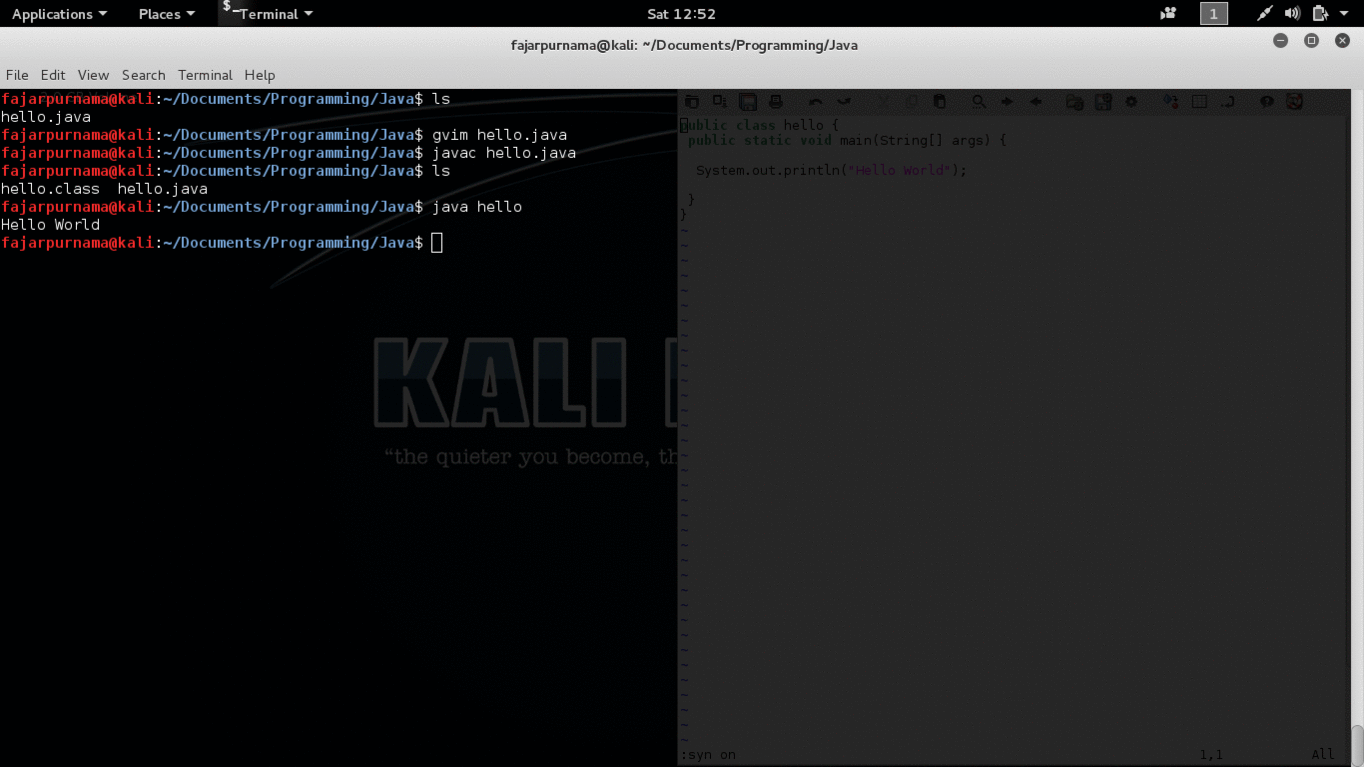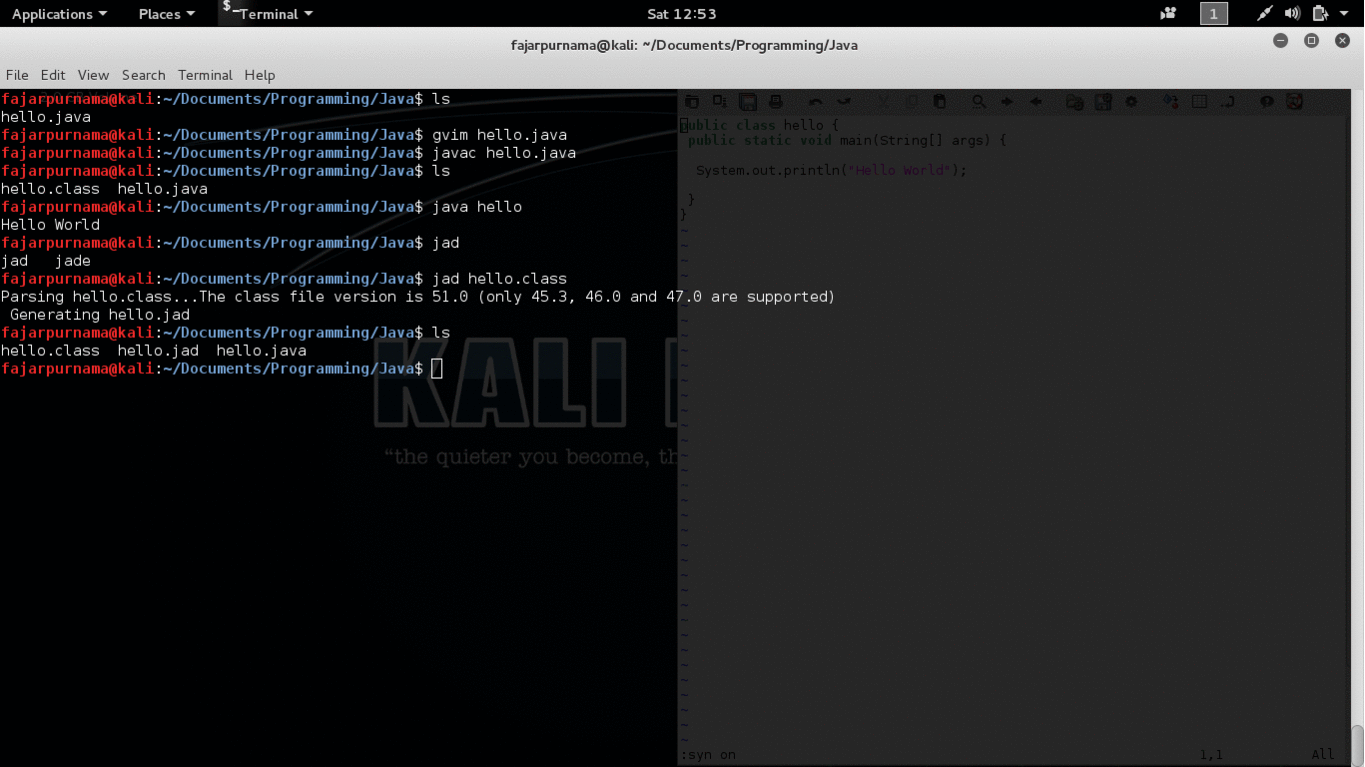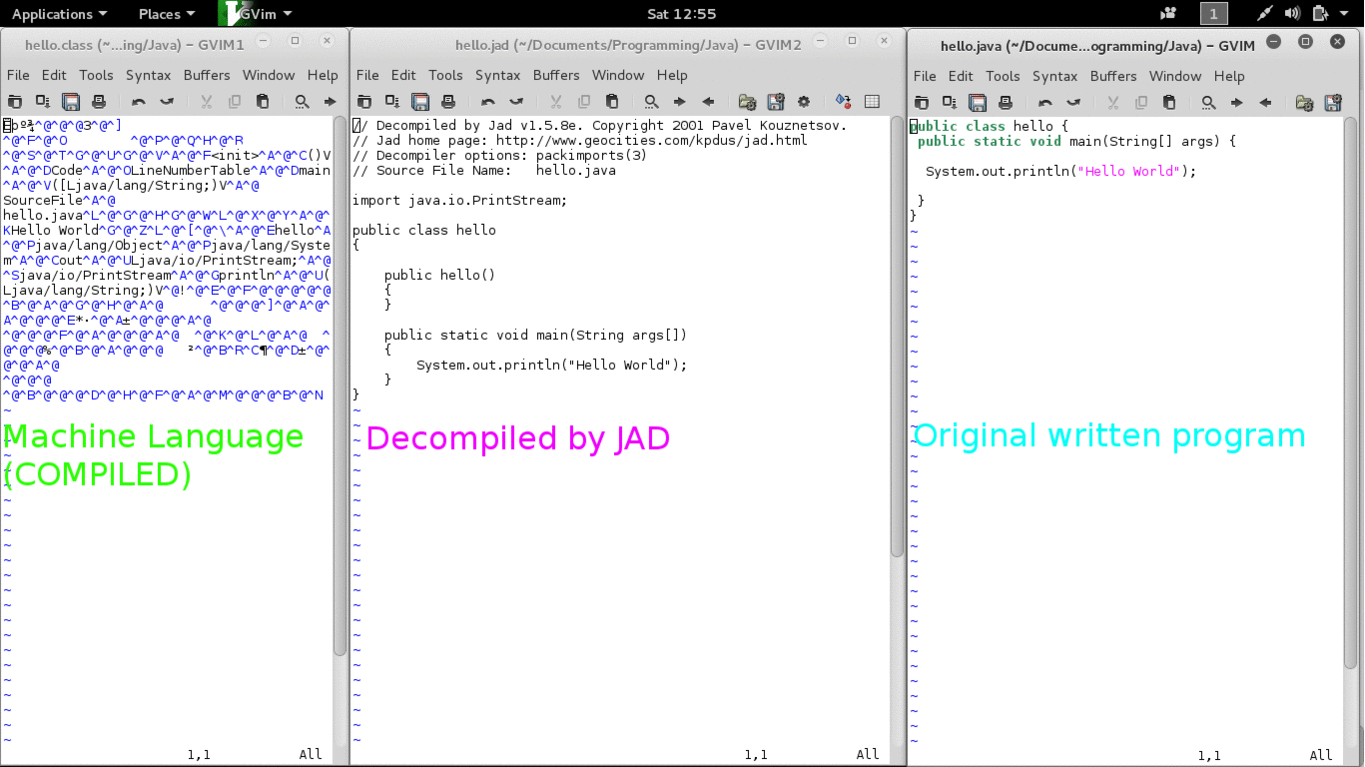
Figure 2. Decompiled Hello Java Program
As stated on the first section that reverse engineering can be used to study and reproduce a software, another important field is that it can be use on computer security, since reverse engineering involves analyzing, dissembling, and may decompile a software. An example of reverse engineering in field of computer security is malware analysis, Figure 3 shows a simple overview of malware analysis through reverse engineering. As an example I experimented in injecting a message box payload using “msfvenom” on “calc.exe” (a calculator software on Windows). On Figure 4 I used Reverse Engineering Compiler (REC) Studio which a software to perform disassembling and decompiling on an executable file to compare the original “calc.exe” and the injected “calc_bdoor.exe”, and shows that another task had been added.

Figure 3. Overview of reverse engineering on malware [3]
Figure 4. Examining executable with recstudio
3. Laws on Reverse Engineering
From [4] reverse engineering has purposes as follows:
Interfacing
Military or commercial espionage
Improve documentation shortcomings
Obsolescence
Software modernization
Product security analysis
Bug fixing
Creation of unlicensed/unapproved duplicates
Academic/learning purposes
Competitive technical intelligence
Saving money
Repurposing
But some regions have strict laws on reverse engineering, mainly copyright issues. The laws on reverse engineering varies each region but also similar. Some permits reverse engineering if the purpose is to fix issues of a software, some permits if it is research and non commercial use, and some permits only if it statet by the software owner on the software that reverse engineering is allowed. [5]
4. Reference
http://www.merriam-webster.com/dictionary/reverse%20engineer
http://www.computerworld.com/article/2585652/app-development/reverse-engineering.html
https://blog.malwarebytes.org/intelligence/2012/09/so-you-want-to-be-a-malware-analyst/
http://www.slideshare.net/welcometofacebook/international-laws-and-reverse-engineering