Barracuda CloudGen firewalls support an unlimited number of VPN clients at no extra cost, making them a cost-effective choice in the WFH era. These VPN tunnels can be set up using their proprietary VPN protocol called TINA. By default it creates two transport tunnels, one over UDP and another over TCP to compensate for the weakness of both protocols. It's really performant and I prefer it over the WireGuard protocol (in business cases) which only supports UDP.
There's one big but, however: Windows 10 feature updates break the software.
The "Barracuda Virtual Adapter" does not get migrated by Windows as it is a virtual network device. Your end-users simply get the error "VPN Adapter not found" when trying to connect:
To fix the problem, you'll need to re-install the Virtual Adapter and this requires administrator rights... Currently there is no other work-around provided by Barracuda that does not involve using admin credentials (source).
This is very troublesome if you have a fleet of laptops traveling the world and no exact timing when a feature update will happen, so let's automate this re-installation.
The solution below has been battle-tested and is working great but use it in your own environment strictly at your own risk.
Let's first create a Powershell script that checks if the Barracuda NAC/VPN Client 5.1.x is installed and if it needs repairing because of a feature update. In this case version 2004. Edit if needed.
Replace the GUID in the script twice with {D8B1A705-3CB7-493C-985D-56C98F6EAEEC} if you're still using version 5.0.x of the VPN software.
if(((Get-ItemProperty -Path "HKLM:\SOFTWARE\Microsoft\Windows NT\CurrentVersion" -Name ReleaseId).ReleaseId) -like "2004"){
if(Test-Path "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\{9056E8A6-FE50-459B-835F-9153F2F0D70F}"){
$install = $true
foreach ($adapter in Get-NetAdapter) {
if($adapter.InterfaceDescription -like "Barracuda Virtual Adapter (VPN)"){
$install = $false
}
}
if($install){
Start-Process -FilePath "$env:systemroot\system32\msiexec.exe" -ArgumentList '/fvomus {9056E8A6-FE50-459B-835F-9153F2F0D70F} /Lecumwvariox setup.log' -Wait
Disable-ScheduledTask -TaskName "Repair Barracuda Virtual Adapter"
}
}
}Next we're setting up a scheduled task which triggers at startup and runs our script.
I prefer this method over regular group policy startup scripts as tasks log to the event log and can easily be audited/debugged. It's also possible to disable our task once it has fixed the issue.
We'll be using a group policy to deploy the script and the scheduled task.
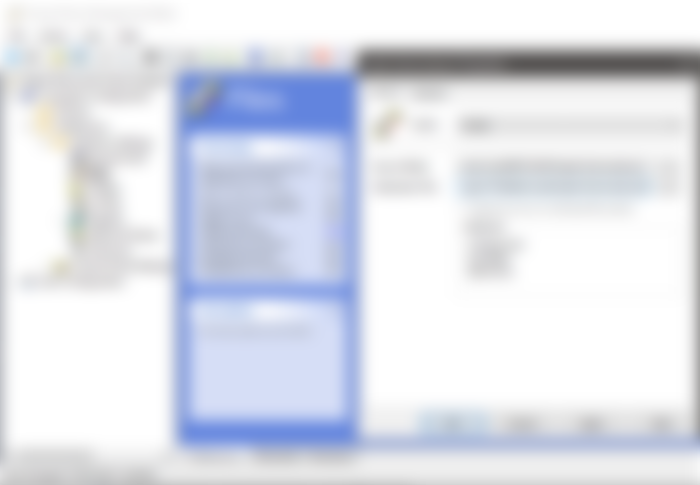
Copying the script to the installation folder of the Barracuda NAC:
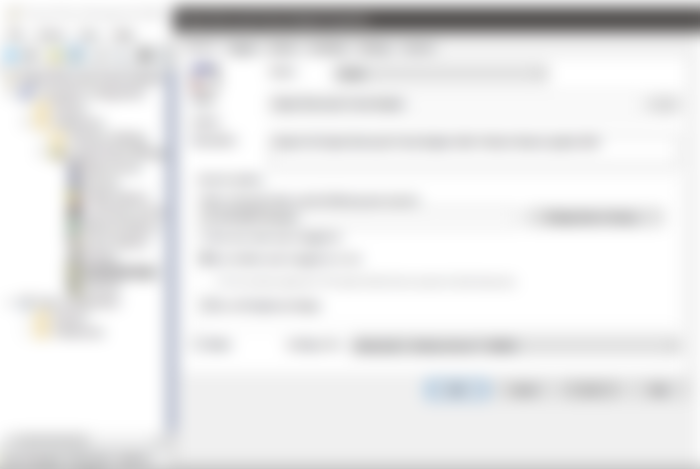
Use the following settings for the scheduled task:
General
Action: Create
User running the task: NT AUTHORITY\System
Check 'Run whether user is logged on or not'
Triggers
At logon of any user
Delay task for: 1 minute
Actions
Start a Program
Program: Powershell.exe
Add arguments: -ExecutionPolicy Bypass -File "C:\Program Files\Barracuda\repair-barracuda.ps1"

If all goes well, the file and scheduled task show up on your endpoints. It will run on startup and will be disabled after repairing the adapter:

If this article was helpful and you're interested in my work, have a look at Folderfay.com. Folderfay manages access rights on traditional Windows file servers and reduces access request to a simple email.